Jammer Mitigation in Multi-Antenna Communications
Smart Jammer Mitigation
In order to remove jammer interference with a spatial filter, a receiver must acquire knowledge of the jammer's spatial signature (e.g., its angle of arrival, when line-of-sight conditions hold; or its subspace; or its spatial covariance matrix). Estimating this spatial signature is easy for barrage jammers that jam continuously and with static transmit strategy. For smart jammers that try to evade estimation, however, estimating that spatial signature is much more challenging. In particular, smart jammers might cease jamming whenever the receiver tries to estimate their signature, or they might use time-varying beamforming (if they have multiple antennas) to continuously change their signature.
In my research, I developed method to mitigate such smart jammers.
In particular, I developed two methods that can perform channel estimation and data detection while mitigating smart jammers. The first of these methods is called joint jammer mitigation and data detection (JMD), and is described in the following papers:
Wireless systems must be resilient to jamming attacks. Existing mitigation methods based on multi-antenna processing require knowledge of the jammer's transmit characteristics that may be difficult to acquire, especially for smart jammers that evade mitigation by transmitting only at specific instants. We propose a novel method to mitigate smart jamming attacks on the massive multi-user multiple-input multiple-output (MU-MIMO) uplink which does not require the jammer to be active at any specific instant. By formulating an optimization problem that unifies jammer estimation and mitigation, channel estimation, and data detection, we exploit that a jammer cannot change its subspace within a coherence interval. Theoretical results for our problem formulation show that its solution is guaranteed to recover the users' data symbols under certain conditions. We develop two efficient iterative algorithms for approximately solving the proposed problem formulation: MAED, a parameter-free algorithm which uses forward-backward splitting with a box symbol prior, and SO-MAED, which replaces the prior of MAED with soft-output symbol estimates that exploit the discrete transmit constellation and which uses deep unfolding to optimize algorithm parameters. We use simulations to demonstrate that the proposed algorithms effectively mitigate a wide range of smart jammers without a priori knowledge about the attack type.
Multi-antenna (MIMO) processing is a promising solution to the problem of jammer mitigation. Existing methods mitigate the jammer based on an estimate of its subspace (or receive statistics) acquired through a dedicated training phase. This strategy has two main drawbacks: (i) it reduces the communication rate since no data can be transmitted during the training phase and (ii) it can be evaded by smart or multi-antenna jammers that are quiet during the training phase or that dynamically change their subspace through time-varying beamforming. To address these drawbacks, we propose Joint jammer Mitigation and data Detection (JMD), a novel paradigm for MIMO jammer mitigation. The core idea is to estimate and remove the jammer interference subspace jointly with detecting the transmit data over multiple time slots. Doing so removes the need for a dedicated and rate-reducing training period while mitigating smart and dynamic multi-antenna jammers. We instantiate our paradigm with SANDMAN, a simple and practical algorithm for multi-user MIMO uplink JMD. Extensive simulations demonstrate the efficacy of JMD, and of SANDMAN in particular, for jammer mitigation.
Whitin the scope of a student project that I supervised, we have also implemented a JMD-type algorithm as an application-specific integrated circuit (ASIC). The resulting chip, Sandman, is not just the first MIMO receiver ASIC that can mitigate smart jammers, but the first MIMO receiver ASIC that mitigates jammers at all. Sandman has been presented at the VLSI Symposium 2024:
We present the first multi-user (MU) multiple-input multiple-output (MIMO) receiver ASIC that mitigates jamming attacks. The ASIC implements a recent nonlinear algorithm that performs joint jammer mitigation (via spatial filtering) and data detection (using a box prior on the data symbols). Our design supports 8 user equipments (UEs) and 32 basestation (BS) antennas, QPSK and 16-QAM with soft-outputs, and enables the mitigation of single-antenna barrage jammers and smart jammers. The fabricated 22 nm FD-SOI ASIC includes preprocessing, has a core area of 3.78 mm2, achieves a throughput of 267 Mb/s while consuming 583 mW, and is the only existing design that enables reliable data detection under jamming attacks

Sandman is the first MIMO receiver ASIC that mitigates jammers. It implements the JMD-type algorithm of the same name, and so can even mitigate smart jammers.
The second method that performs channel estimation and data detection while mitigating smart jammers is mitigation via subspace hiding (MASH), and is described in this paper:
MIMO processing enables jammer mitigation through spatial filtering, provided that the receiver knows the spatial signature of the jammer interference. Estimating this signature is easy for barrage jammers that transmit continuously and with static signature, but difficult for more sophisticated jammers: Smart jammers may deliberately suspend transmission when the receiver tries to estimate their spatial signature, they may use time-varying beamforming to continuously change their spatial signature, or they may stay mostly silent and jam only specific instants (e.g., transmission of control signals). To deal with such smart jammers, we propose MASH, the first method that indiscriminately mitigates all types of jammers: Assume that the transmitter and receiver share a common secret. Based on this secret, the transmitter embeds (with a linear time-domain transform) its signal in a secret subspace of a higher-dimensional space. The receiver applies a reciprocal linear transform to the receive signal, which (i) raises the legitimate transmit signal from its secret subspace and (ii) provably transforms any jammer into a barrage jammer, which makes estimation and mitigation via MIMO processing straightforward. We show the efficacy of MASH for data transmission in the massive multi-user MIMO uplink.
Communication requries more than channel estimation and data detection, however. In fact, before channel estimation and data detection can even begin, medium access control and synchronization need to be achieved. Under (smart) jamming, these tasks also become much harder. Together with a student whose thesis I have supervised, I have proposed a method for time-synchronization in the face of smart jamming attacks, called JASS. The method is described in the following paper which is currently under review:
Spatial filtering based on multiple-input multiple-output (MIMO) processing is a promising approach to jammer mitigation. Effective MIMO data detectors that mitigate smart jammers have recently been proposed, but they all assume perfect time synchronization between transmitter(s) and receiver. However, to the best of our knowledge, there are no methods for resilient time synchronization in the presence of smart jammers. To remedy this situation, we propose JASS, the first method that enables reliable time synchronization for the single-user MIMO uplink while mitigating smart jamming attacks. JASS detects a randomized synchronization sequence based on a novel optimization problem that fits a spatial filter to the time-windowed receive signal in order to mitigate the jammer. We underscore the efficacy of the proposed optimization problem by proving that it ensures successful time synchronization under certain intuitive conditions. We then derive an efficient algorithm for approximately solving our optimization problem. Finally, we use simulations to demonstrate the effectiveness of JASS against a wide range of different jammer types.
The above methods for MIMO jammer mitigation are digital, meaning that they operate on the digitized version of the receive signal. Moreover, they are based on a linear signal model: they assume that the digital receive signal is a linear superposition of the legitimate communication signal, the jammer interference, and the noise.
However, converting the analog receive signal into the digital domain necessarily involves nonlinear quantization, which is at odds with a linear signal model. In my reseach, I have proved information-theoretically that strong jammers exacerbate the adverse impact of quantization noise, and that the resolution of the quantization must improve by 1 bit for every 6.02dB of additional jamming power in order for digital jammer mitigation to remain possible:
Spatial filtering based on multiple-input multiple-output (MIMO) processing is a powerful method for jammer mitigation. In principle, a MIMO receiver can null the interference of a single-antenna jammer at the cost of only one degree of freedom - if the number of receive antennas is large, communication performance is barely affected. In this paper, we show that the potential for MIMO jammer mitigation based on the digital outputs of finite-resolution analog-to-digital converters (ADCs) is fundamentally worse: Strong jammers will either cause the ADCs to saturate (when the ADCs' quantization range is small) or drown legitimate communication signals in quantization noise (when the ADCs' quantization range is large). We provide a fundamental bound on the mutual information between the quantized receive signal and the legitimate transmit signal. Our bound shows that, for any fixed ADC resolution, the mutual information tends to zero as the jammer power tends to infinity. Our bound also confirms the intuition that for every 6.02 dB increase in jamming power, the ADC resolution must be increased by 1 bit in order to prevent the mutual information from vanishing.
The issue of quantization noise is essentially pronounced in millimeter-wave (mmWave) massive MIMO systems, which are expected to rely on low-resolution analog-to-digital converters (ADCs). To alleviate the issue of exacerbated quantization noise, we have proposed hybrid methods where the jammer interference is largely prevented from reaching the ADCs through analog processing:
Low-resolution analog-to-digital converters (ADCs) simplify the design of millimeter-wave (mmWave) massive multi-user multiple-input multiple-output (MU-MIMO) basestations, but increase vulnerability to jamming attacks. As a remedy, we propose HERMIT (short for Hybrid jammER MITigation), a method that combines a hardware-friendly adaptive analog transform with a corresponding digital equalizer: The analog transform removes most of the jammer’s energy prior to data conversion; the digital equalizer suppresses jammer residues while detecting the legitimate transmit data. We provide theoretical results that establish the optimal analog transform as a function of the user equipments’ and the jammer’s channels. Using simulations with mmWave channel models, we demonstrate the superiority of HERMIT compared both to purely digital jammer mitigation as well as to a recent hybrid method that mitigates jammer interference with a nonadaptive analog transform. Millimeter-wave (mmWave) massive multi-user multiple-input multiple-output (MU-MIMO) promises unprecedented data rates for next-generation wireless systems. To be practically viable, mmWave massive MU-MIMO basestations (BSs) must rely on low-resolution data converters which leaves them vulnerable to jammer interference. This paper proposes beam-slicing, a method that mitigates the impact of a permanently transmitting jammer during uplink transmission for BSs equipped with low-resolution analog-to-digital converters (ADCs). Beam-slicing is a localized analog spatial transform that focuses the jammer energy onto few ADCs, so that the transmitted data can be recovered based on the outputs of the interference-free ADCs. We demonstrate the efficacy of beam-slicing in combination with two digital jammer-mitigating data detectors: SNIPS and CHOPS. Soft-Nulling of Interferers with Partitions in Space (SNIPS) combines beam-slicing with a soft-nulling data detector that exploits knowledge of the ADC contamination; projeCtion onto ortHOgonal complement with Partitions in Space (CHOPS) combines beam-slicing with a linear projection that removes all signal components co-linear to an estimate of the jammer channel. Our results show that beam-slicing enables SNIPS and CHOPS to successfully serve 65% of the user equipments (UEs) for scenarios in which their antenna-domain counterparts that lack beam-slicing are only able to serve 2% of the UEs.
Whitin the scope of a Master's thesis that I supervised, we wanted to leverage the power of machine learning for understanding jamming and jammer mitigation. For this, we developed PyJama, an open-source library built on top of NVIDIA Sionna. PyJama brings jamming and anti-jamming capabilites to NVIDIA Sionna, and it does so in fully differentiable fashion. We then used PyJama for learning to jam, specifically, for learning how to optimally allocate jamming energy to different OFDM symbols. The PyJama library, as well as our results, are described in the following paper:
Despite extensive research on jamming attacks on wireless communication systems, the potential of machine learning for amplifying the threat of such attacks, or our ability to mitigate them, remains largely untapped. A key obstacle to such research has been the absence of a suitable framework. To resolve this obstacle, we release PyJama, a fully-differentiable open-source library that adds jamming and anti-jamming functionality to NVIDIA Sionna. We demonstrate the utility of PyJama (i) for realistic MIMO simulations by showing examples that involve forward error correction, OFDM waveforms in time and frequency, realistic channel models, and mobility; and (ii) for learning to jam. Specifically, we use stochastic gradient descent to optimize jamming power allocation over an OFDM resource grid. The learned strategies are non-trivial, intelligible, and effective.
I also investigated what happens in OFDM-MIMO under jamming when jammers violate the cyclic-prefix structure required by OFDM. It turns out that single-antenna jammers, whose interference would occupy a one-dimensional subspace of the signal space as long as the channels are frequency-flat, can occupy a subspace with dimension up to \(L\) when the channels are time-dispersive (where \(L\) is the number of non-zero channel taps). Thus, single-antenna jammers look like multi-antenna jammers, and are therefore harder to mitigate. The issue is expounded in the following paper:
In multiple-input multiple-output (MIMO) wireless systems with frequency-flat channels, a single-antenna jammer causes receive interference that is confined to a one-dimensional subspace. Such a jammer can thus be nulled using linear spatial filtering at the cost of one degree of freedom. Frequency-selective channels are often transformed into multiple frequency-flat subcarriers with orthogonal frequency-division multiplexing (OFDM). We show that when a single-antenna jammer violates the OFDM protocol by not sending a cyclic prefix, the interference received on each subcarrier by a multi-antenna receiver is, in general, not confined to a subspace of dimension one (as a single-antenna jammer in a frequency-flat scenario would be), but of dimension L, where L is the jammer's number of channel taps. In MIMO-OFDM systems, a single-antenna jammer can therefore resemble an L-antenna jammer. Simulations corroborate our theoretical results. These findings imply that mitigating jammers with large delay spread through linear spatial filtering is infeasible. We discuss some (im)possibilities for the way forward.
Jammer Mitigation in Finite- and Low-Resolution MIMO
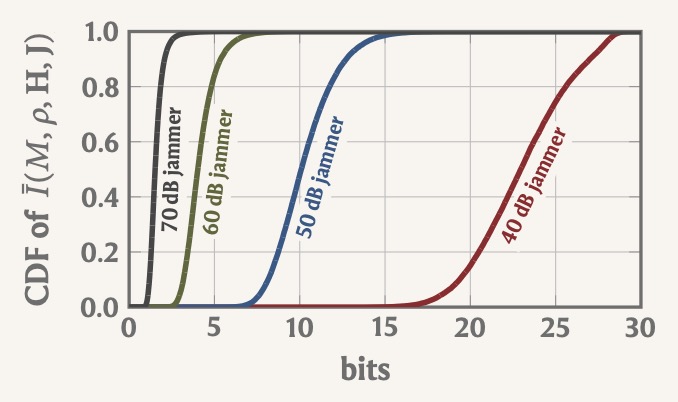
The mutual information between finite-resolution receive signals and legitimate transmit signals decreases as the jammer power increases.
This figure shows cumulative distribution functions (CDFs) of an upper bound on said mutual information for a MIMO receiver with 2bit ADCs.
Other Topics in MIMO Jammer Mitigation
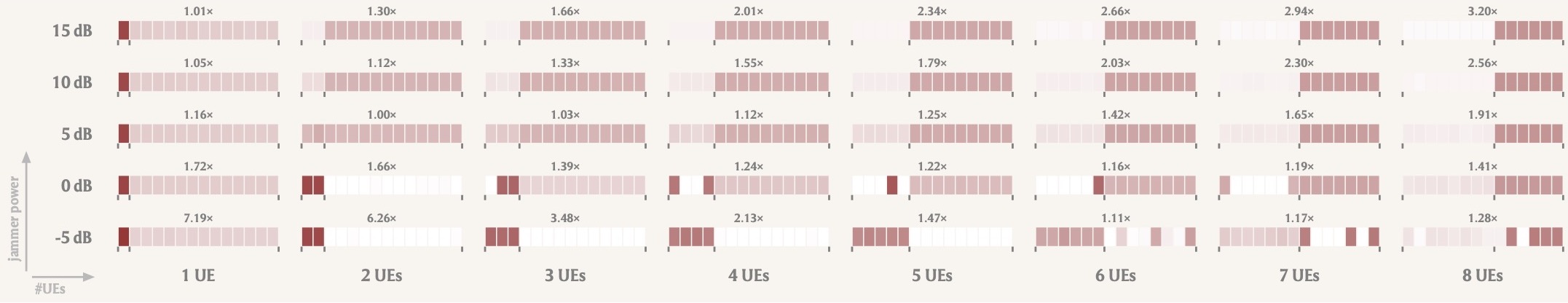 How to optimally allocate jamming power to different OFDM symbols depends on the total energy budget and on the number of user equipments (UEs) that are simultanously active in the attacked multi-user MIMO uplink system.
How to optimally allocate jamming power to different OFDM symbols depends on the total energy budget and on the number of user equipments (UEs) that are simultanously active in the attacked multi-user MIMO uplink system.
← home









